forked from SpiderLabs/Responder
-
-
Notifications
You must be signed in to change notification settings - Fork 785
Network traffic analyze mode
lgandx edited this page Apr 21, 2021
·
3 revisions
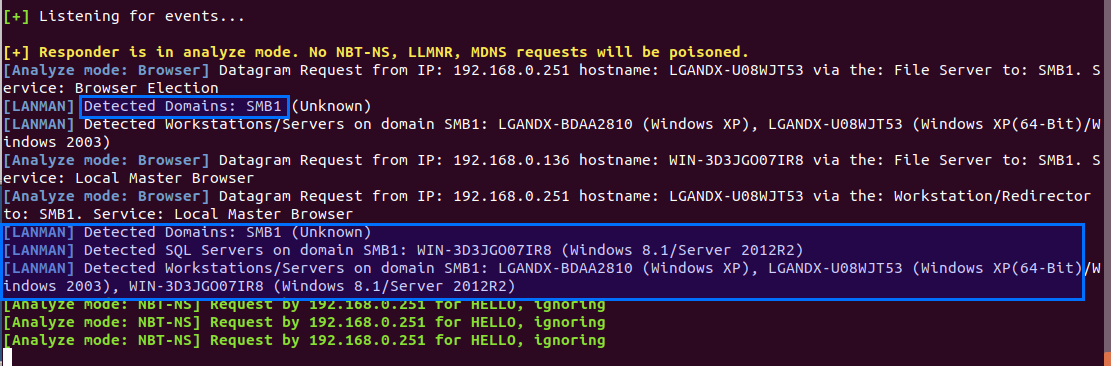
Responder has a built-in functionality which allows you to monitor without poisoning anything what is going on the subnet. This mode allows you to see who is looking for what on the network, and consequently build an attack.
This mode also has a Browser protocol listener analyzing all Browser protocol messages (port 138) and performs Browser backup requests to retrieve the complete list of workstation name and capabilities (server, workstation, mssql, PDC, etc) on the network.
Responder's analyze mode can be used by clients who want to see if NBT-NS/LLMNR remediation was successful or not, prior a retest.
To launch Responder in Analyze mode, use the following command:
./Responder.py -I eth0 -A